Attackers have an over-growing list of vulnerabilities to exploit in order to maliciously gain access to your web applications, networks and servers. Whether you’re a novice WordPress user or a sophisticated hosting service, if truly determined then an attacker will find any vulnerability you’ve failed to patch and use it to their advantage.
New vulnerabilities are being discovered all the time; by security researchers, by attackers, even by users. Each time changes are made at any level of the infrastructure, there’s the potential for new vulnerabilities to be created.
Web applications are susceptible to attacks that may result in exposure or modification of sensitive data, or impact on availability of services to authorized users. Application testing is conducted to identify security flaws introduced in the design, implementation or deployment of an application. Developers and application administrators must identify functions that are critical to security, and test those functions to verify correct operation.
One of the unique features of ZAP is that its sensitivity and scan aggressiveness can be manually configured. There are three sensitivity settings (high, medium and low). For example, if having a high number of false positives is a problem for you set the alert threshold to high. The risk here obviously is you would increase your false negatives (I.e.: there would be vulnerabilities that you would miss).
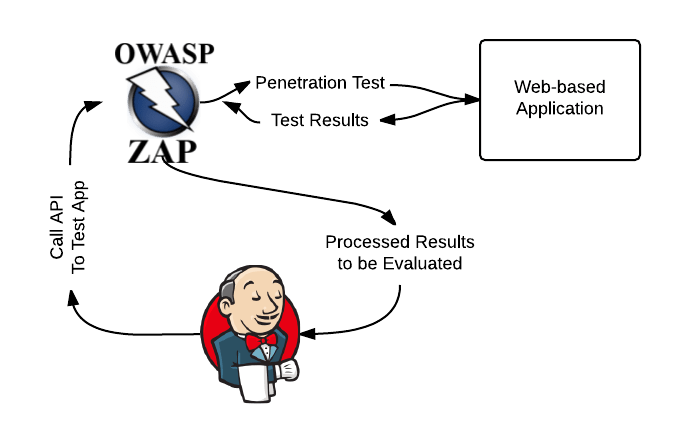
OWASP ZAP is the swiss army knife of web assessment tools. ZAP’s active scanner is integrated in to many of the other functions of the application so it is misleading to discuss ZAP as a scanner only. Having a proxy and these other tools built in is a huge plus.
